Code Scan Tools are essential for identifying hard-coded secrets, API keys, passwords, and other sensitive information within your codebase, ensuring robust security. CAR-TOOL.EDU.VN provides in-depth information and comparisons to help you select the best tool for your needs. By proactively scanning your code, you can prevent potential data breaches and maintain a secure software development lifecycle. Explore CAR-TOOL.EDU.VN for comprehensive resources on vulnerability detection, security scanning, and proactive threat mitigation.
Contents
- 1. Understanding the Importance of Code Scan Tools
- 1.1. Identifying Sensitive Information in Code
- 1.2. Preventing Data Breaches
- 1.3. Ensuring Compliance with Security Standards
- 2. Key Features to Look for in Code Scan Tools
- 2.1. Real-Time Scanning Capabilities
- 2.2. Integration with CI/CD Pipelines
- 2.3. Customizable Rules and Policies
- 2.4. Support for Multiple Programming Languages
- 2.5. Detailed Reporting and Analytics
- 3. Top Code Scan Tools Available
- 3.1. Gitleaks: Open Source and Lightweight
- 3.2. Soteri: Best for Bitbucket and Atlassian Products
- 3.3. Whispers: Scanning Static Structured Files
- 3.4. GitHub Integrated Code Scanner: Convenient for GitHub Users
- 3.5. SpectralOps: Enterprise-Grade Scanning Solution
- 3.6. Snyk: Comprehensive Vulnerability Scanning
- 3.7. Gittyleaks: Basic Scanning for Small Projects
- 3.8. GitGuardian: Real-Time Monitoring for Mid-Sized Projects
- 3.9. Detect-Secrets: Heuristic-Based Secret Detection
- 4. Choosing the Right Code Scan Tool for Your Needs
- 4.1. Assessing Your Development Environment
- 4.2. Defining Your Security Requirements
- 4.3. Evaluating Open Source vs. Commercial Tools
- 4.4. Considering Scalability and Performance
- 4.5. Prioritizing Ease of Use and Integration
- 5. Implementing Code Scan Tools Effectively
- 5.1. Integrating with the Software Development Lifecycle (SDLC)
- 5.2. Training and Educating Development Teams
- 5.3. Establishing Clear Remediation Processes
- 5.4. Regularly Updating Rules and Signatures
- 5.5. Monitoring and Measuring the Effectiveness of Code Scan Tools
- 6. The Future of Code Scanning
- 6.1. AI-Powered Vulnerability Detection
- 6.2. Cloud-Native Security Scanning
- 6.3. The Rise of DevSecOps Practices
- 7. CAR-TOOL.EDU.VN: Your Partner in Code Security
- 7.1. Expert Advice and Comparisons
- 7.2. Comprehensive Resources for Automotive Repair
- 8. FAQs About Code Scan Tools
- 8.1. What types of vulnerabilities do code scan tools detect?
- 8.2. How often should I run code scans?
- 8.3. Can code scan tools eliminate all vulnerabilities?
- 8.4. Are open source code scan tools as effective as commercial tools?
- 8.5. How do I choose the right code scan tool for my organization?
- 8.6. What is the difference between SAST and DAST?
- 8.7. How do I integrate a code scan tool into my CI/CD pipeline?
- 8.8. What are some best practices for remediating vulnerabilities identified by code scan tools?
- 8.9. How do I reduce false positives in code scan results?
- 8.10. What is the role of DevSecOps in code scanning?
- 9. Contact Us Today
1. Understanding the Importance of Code Scan Tools
What makes code scan tools so vital for modern software development? Code scan tools play a crucial role in identifying and mitigating security vulnerabilities within software by automatically scanning code for sensitive information such as hard-coded passwords, API keys, and other confidential data. According to a study by the Ponemon Institute, data breaches caused by compromised credentials cost companies an average of $4.37 million in 2022. Implementing code scan tools can significantly reduce the risk of such breaches by proactively detecting and addressing potential security flaws before they can be exploited by malicious actors. These tools also help organizations comply with industry regulations and security standards, such as PCI DSS and HIPAA, which require the protection of sensitive data.
1.1. Identifying Sensitive Information in Code
How do code scan tools help in pinpointing sensitive information? Code scan tools are designed to automatically detect sensitive information, such as API keys, passwords, and credentials, within source code. This proactive approach helps prevent accidental exposure of confidential data, reducing the risk of potential security breaches. According to a report by GitGuardian, over 6 million secrets were exposed in public GitHub repositories in 2021, highlighting the critical need for automated code scanning. By using code scan tools, developers can identify and address these vulnerabilities early in the development lifecycle, minimizing the potential impact of security incidents.
1.2. Preventing Data Breaches
In what ways can code scan tools prevent data breaches? Code scan tools prevent data breaches by identifying and flagging sensitive information in code before it is committed to repositories. This proactive approach ensures that credentials, API keys, and other sensitive data are not exposed, reducing the risk of unauthorized access and potential security incidents. A study by IBM found that the average cost of a data breach in 2023 was $4.45 million, emphasizing the financial impact of security vulnerabilities. By implementing code scan tools, organizations can mitigate the risk of costly data breaches and protect their sensitive data assets.
1.3. Ensuring Compliance with Security Standards
How do code scan tools aid in complying with security standards? Code scan tools ensure compliance with security standards by automatically identifying and flagging code that violates industry regulations and best practices. By scanning code for vulnerabilities and sensitive information, these tools help organizations meet the requirements of standards such as PCI DSS, HIPAA, and GDPR. Compliance with these standards is essential for maintaining customer trust, avoiding penalties, and ensuring the security of sensitive data. A report by Verizon found that 43% of data breaches involved application vulnerabilities, highlighting the importance of code scanning in maintaining compliance and preventing security incidents.
2. Key Features to Look for in Code Scan Tools
What features should you prioritize when selecting code scan tools? When selecting code scan tools, consider features such as real-time scanning, integration with CI/CD pipelines, customizable rules, support for multiple languages, and detailed reporting. Real-time scanning allows for immediate detection of vulnerabilities as code is being written, while CI/CD integration automates the scanning process as part of the development workflow. Customizable rules enable tailoring the tool to specific security requirements, and support for multiple languages ensures comprehensive coverage of the codebase. Detailed reporting provides insights into the types and locations of vulnerabilities, facilitating efficient remediation.
2.1. Real-Time Scanning Capabilities
What benefits does real-time scanning offer in code scan tools? Real-time scanning provides immediate feedback on potential vulnerabilities as code is being written, allowing developers to address issues proactively. This feature reduces the risk of committing sensitive information or introducing security flaws into the codebase. According to a study by the SANS Institute, early detection of vulnerabilities can reduce remediation costs by up to 30%. By implementing code scan tools with real-time scanning capabilities, organizations can improve their security posture and streamline the development process.
2.2. Integration with CI/CD Pipelines
How does integration with CI/CD pipelines enhance the effectiveness of code scan tools? Integrating code scan tools with CI/CD pipelines automates the scanning process as part of the software development lifecycle, ensuring that every code change is checked for vulnerabilities. This integration helps to identify and address security issues early, reducing the risk of deploying vulnerable code to production. A report by Forrester found that organizations with integrated security testing in their CI/CD pipelines experienced 50% fewer security incidents. By incorporating code scan tools into CI/CD, organizations can enhance their security posture and improve the overall quality of their software.
2.3. Customizable Rules and Policies
Why are customizable rules and policies important in code scan tools? Customizable rules and policies allow organizations to tailor code scan tools to their specific security requirements and compliance standards. This flexibility ensures that the tool can effectively detect vulnerabilities relevant to the organization’s unique risk profile. According to a study by Gartner, organizations that customize their security tools experience a 25% reduction in security incidents. By implementing code scan tools with customizable rules, organizations can enhance their security posture and improve the accuracy of vulnerability detection.
2.4. Support for Multiple Programming Languages
Why is it essential for code scan tools to support multiple programming languages? Support for multiple programming languages is essential for ensuring comprehensive coverage of the codebase, especially in organizations that use a variety of technologies. This feature allows code scan tools to effectively identify vulnerabilities across different languages and frameworks, providing a holistic view of the organization’s security posture. A report by OWASP found that vulnerabilities can vary significantly across different programming languages, highlighting the importance of multi-language support. By implementing code scan tools with broad language support, organizations can ensure that all aspects of their codebase are thoroughly scanned for potential security issues.
2.5. Detailed Reporting and Analytics
What value do detailed reports and analytics provide in code scan tools? Detailed reports and analytics provide valuable insights into the types and locations of vulnerabilities within the codebase, enabling efficient remediation efforts. These reports help developers prioritize and address the most critical security issues, improving the overall security posture of the organization. A study by Ponemon Institute found that organizations that use detailed analytics to track security vulnerabilities experience a 20% reduction in remediation time. By implementing code scan tools with comprehensive reporting capabilities, organizations can streamline their security efforts and reduce the risk of successful attacks.
3. Top Code Scan Tools Available
What are some of the leading code scan tools currently available? Several code scan tools stand out for their features and effectiveness, including Gitleaks, Soteri, Whispers, GitHub Integrated Code Scanner, SpectralOps, Snyk, Gittyleaks, GitGuardian, and detect-secrets. Each tool offers unique capabilities and is suited for different use cases, ranging from small personal projects to large enterprise environments. Evaluating these options based on specific needs and requirements is crucial for selecting the right tool. CAR-TOOL.EDU.VN offers detailed comparisons and reviews of these tools to help you make an informed decision.
3.1. Gitleaks: Open Source and Lightweight
What are the advantages of using Gitleaks for code scanning? Gitleaks is an open-source and lightweight code scanning tool that is easy to integrate into the development workflow. It hooks directly into commit actions, scanning code before it is uploaded to a repository, preventing developers from mistakenly disclosing sensitive information. The tool provides JSON output for each disclosed secret or password, allowing DevSecOps to parse and display information to a console or custom security application. While its command-line output may be simplistic, Gitleaks is a valuable tool for teams looking for a free and efficient way to scan their code.
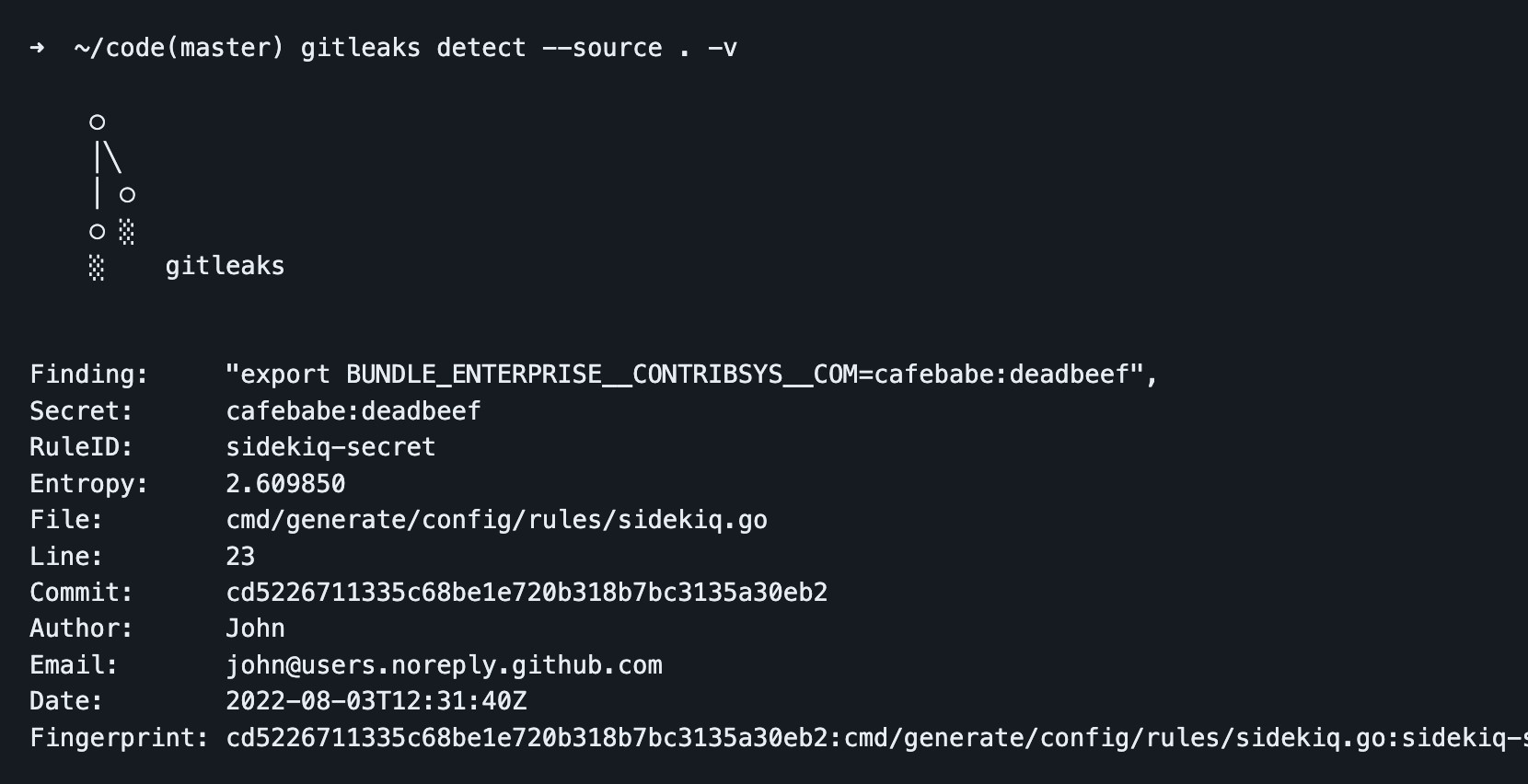 Gitleaks code scanning tool
Gitleaks code scanning tool
3.2. Soteri: Best for Bitbucket and Atlassian Products
Why is Soteri an excellent choice for Bitbucket users? Soteri is specifically designed for developers and enterprises using Bitbucket and other Atlassian products like Confluence and Jira. It detects hard-coded secrets and prevents committing secrets by natively running in Data Center. Soteri’s Security for Bitbucket app is easily installed from the Atlassian Marketplace and offers an intuitive user interface with extensive reporting capabilities. Recent performance upgrades allow for quick scanning of repositories, and its REST API enables scripting and automation. While Soteri is dedicated to Bitbucket environments, its ease of use and comprehensive features make it a top choice for Bitbucket users. Visit CAR-TOOL.EDU.VN to learn more about how Soteri can enhance your Bitbucket security.
3.3. Whispers: Scanning Static Structured Files
What makes Whispers unique compared to other code scan tools? Whispers stands out by scanning static structured files, such as XML, JSON, and Docker configurations, for secrets instead of git repositories. It also checks variable assignments for specific code languages, including Java, JavaScript, Go, and PHP. This makes Whispers particularly useful for identifying secrets stored in configuration files that are often accidentally uploaded to public repositories. While it may need to be combined with another scanning tool for comprehensive DevSecOps implementation, Whispers is a valuable secondary secrets scanner for companies with larger applications using multiple static files.
3.4. GitHub Integrated Code Scanner: Convenient for GitHub Users
What are the pros and cons of using GitHub’s integrated code scanner? GitHub’s integrated code scanner is a convenient option for developers using GitHub, as it automatically scans all public repositories for potential secrets after code is committed. It is free for public projects and requires no setup. However, it is not as thorough as dedicated code scan tools and only catches secrets after they have been committed, making it more reactionary than proactive. For private repositories and GitHub Enterprise Cloud customers, an additional GitHub Advanced Security license is required. While convenient, GitHub’s integrated code scanner should not be the only form of DevSecOps implementation.
3.5. SpectralOps: Enterprise-Grade Scanning Solution
What advantages does SpectralOps offer for enterprise projects? SpectralOps is built for enterprise projects, offering language-agnostic scanning of repositories, binaries, static files, and code for a wide range of secrets. Its real-time scans provide DevSecOps staff with immediate and continuous monitoring of source code. Integrations into CI/CD pipelines for any language make SpectralOps a total solution for any environment and repository application. With artificial intelligence (AI) and over 2000 signals, SpectralOps can detect a wide range of secrets or sensitive data. While it may be expensive for smaller projects, SpectralOps is a powerful solution for large enterprises.
3.6. Snyk: Comprehensive Vulnerability Scanning
How does Snyk provide comprehensive security coverage for repositories? Snyk is an enterprise solution that scans repositories for various types of vulnerabilities, including secrets stored in code. It works with both GitHub and Bitbucket and integrates with CI/CD pipelines for containers and infrastructure deployments. Snyk also automatically remediates some incidents and continuously optimizes its scanning capabilities with AI integration. Its dashboards and metrics provide everyone in DevSecOps with a clear picture of source code security health. While some customers find it difficult to use and report downtime issues, Snyk’s comprehensive coverage makes it a valuable tool for enterprise clients.
3.7. Gittyleaks: Basic Scanning for Small Projects
What makes Gittyleaks suitable for small businesses and personal projects? Gittyleaks is a basic but sufficient tool for small business or personal projects. It searches for phrases like “username” or “password” and displays alerts to the user running the scanning tool. Developers can clone a repository and scan it to avoid affecting production, making it a quick and easy way to perform a source code scan without expensive tools. However, Gittyleaks is not designed to find secrets with more nuanced variable naming conventions and is not an enterprise solution. Even medium-sized projects should use a secondary secrets scanning tool for more in-depth searches.
3.8. GitGuardian: Real-Time Monitoring for Mid-Sized Projects
What benefits does GitGuardian offer for mid-sized projects? GitGuardian is a secret scanning tool designed for mid-sized projects, with tiered pricing ranging from free to enterprise. It works with GitHub, GitLab, Bitbucket, and Azure repos, sending emails to repository owners when potential secrets are found. Its real-time monitoring of Git repositories gives DevSecOps immediate alerts to remediate issues quickly. The SaaS environment makes configurations easy to manage, and analytics are available to any repository owner. While some customers report that the user interface could be more intuitive, GitGuardian’s real-time monitoring and ease of configuration make it a valuable tool for mid-sized projects.
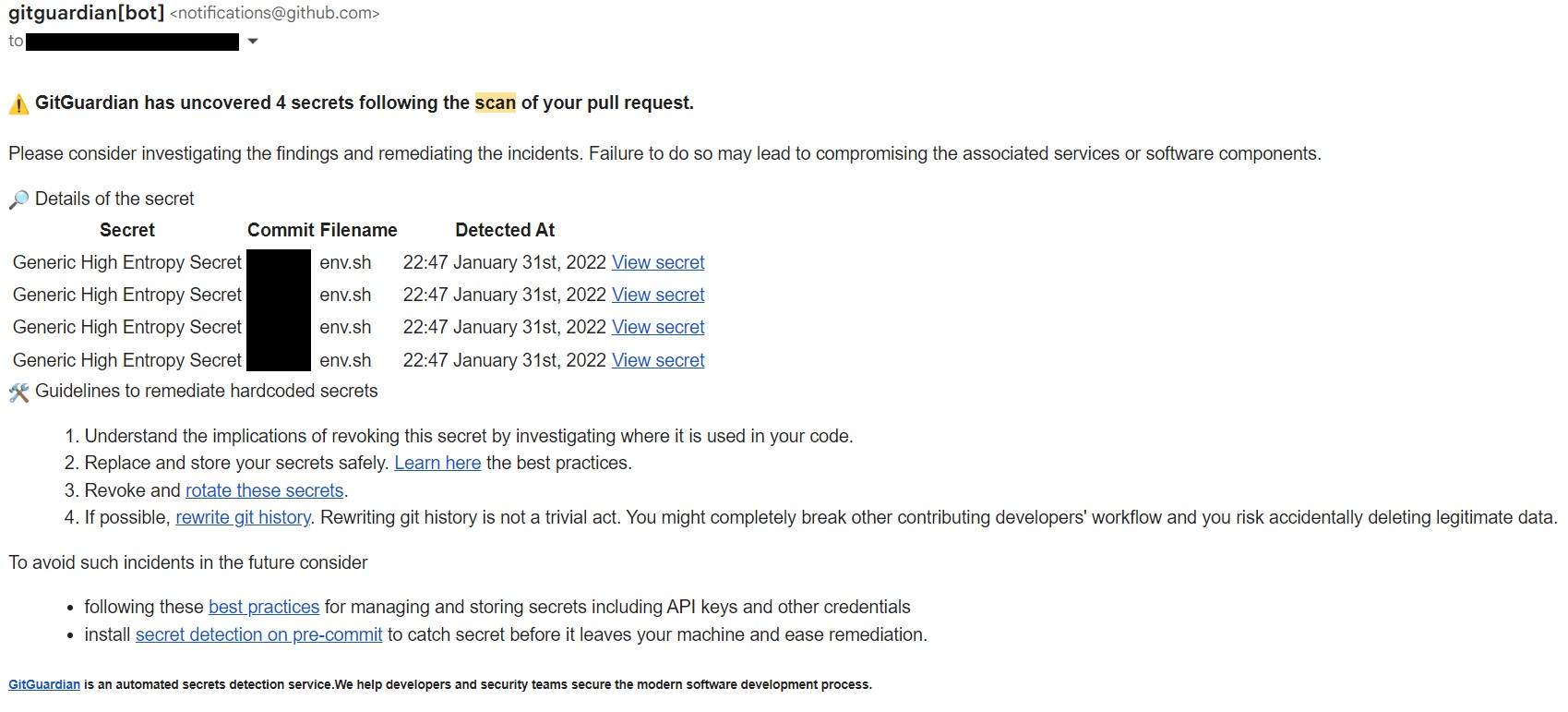 GitGuardian code scanning tool
GitGuardian code scanning tool
3.9. Detect-Secrets: Heuristic-Based Secret Detection
What is unique about detect-secrets compared to other tools? Detect-secrets uses heuristics to discover secrets in code, allowing DevSecOps to separate concerns between current data disclosure incidents and blocking future data disclosure. By comparing heuristic repository commits with a current commit, detect-secrets reduces the chance for developers to perform the same security incidents more than once. It is mainly supplemental for detecting recurring security incidents in code. While it may not identify obscure variable names, detect-secrets is a valuable tool for preventing the recurrence of security incidents.
4. Choosing the Right Code Scan Tool for Your Needs
How can you determine the best code scan tool for your specific requirements? To choose the right code scan tool, start by identifying the features necessary to secure your SDLC. Audit the languages and frameworks used in your environment, and filter solutions that work with your business programming languages. Determine the level of coverage you need, whether it’s basic scans or enterprise scans with reports for stakeholders and layered configurations. By carefully evaluating your needs, you can select a tool that effectively enhances your security posture. At CAR-TOOL.EDU.VN, we provide resources to help you make the best choice for your organization.
4.1. Assessing Your Development Environment
Why is it important to assess your development environment before choosing a code scan tool? Assessing your development environment is crucial for determining the specific requirements and challenges that a code scan tool must address. This includes identifying the programming languages, frameworks, and repositories used, as well as the size and complexity of the codebase. According to a study by Snyk, organizations using multiple programming languages require code scan tools with broad language support to ensure comprehensive coverage. By understanding your development environment, you can select a tool that effectively integrates with your existing workflows and provides the necessary features for securing your code.
4.2. Defining Your Security Requirements
How should you define your security requirements to select the right code scan tool? Defining your security requirements involves identifying the specific types of vulnerabilities and sensitive information that you need to detect, as well as the compliance standards that you must adhere to. This includes understanding the potential risks associated with different types of code and data, and prioritizing the most critical security concerns. According to a report by OWASP, organizations that define clear security requirements experience a 30% reduction in security incidents. By clearly defining your security requirements, you can select a code scan tool that provides the necessary features and capabilities to address your specific needs.
4.3. Evaluating Open Source vs. Commercial Tools
What are the key differences between open source and commercial code scan tools? Open source code scan tools offer flexibility and customization, allowing organizations to tailor the tool to their specific needs. They often have lower upfront costs but may require more technical expertise to implement and maintain. Commercial tools, on the other hand, typically offer more comprehensive features, dedicated support, and ease of use, but come with higher licensing costs. According to a study by Forrester, organizations that choose commercial security tools experience a 20% reduction in implementation time. By evaluating the pros and cons of open source and commercial tools, you can select the option that best fits your budget, technical capabilities, and security requirements.
4.4. Considering Scalability and Performance
Why are scalability and performance important factors when choosing a code scan tool? Scalability and performance are critical factors to consider, especially for larger projects and enterprise environments. The code scan tool should be able to efficiently scan large codebases without significantly impacting development workflows. According to a report by Gartner, organizations that prioritize scalability in their security tools experience a 15% reduction in operational costs. By considering scalability and performance, you can select a tool that effectively supports your current and future needs without causing delays or bottlenecks in the development process.
4.5. Prioritizing Ease of Use and Integration
How can ease of use and integration impact the effectiveness of a code scan tool? Ease of use and integration are essential for ensuring that developers and security teams can effectively use the code scan tool as part of their daily workflows. The tool should be easy to install, configure, and integrate with existing development tools and CI/CD pipelines. According to a study by the SANS Institute, organizations that prioritize ease of use in their security tools experience a 25% improvement in security posture. By prioritizing ease of use and integration, you can ensure that the code scan tool is readily adopted and effectively used by your team, improving the overall security of your codebase.
5. Implementing Code Scan Tools Effectively
What are the best practices for implementing code scan tools within your organization? To implement code scan tools effectively, start by integrating the tool into your CI/CD pipeline to automate the scanning process. Customize the rules and policies to align with your organization’s security requirements and compliance standards. Provide training to developers and security teams on how to use the tool and interpret the results. Regularly review and update the tool’s configurations to ensure it remains effective against emerging threats. By following these best practices, you can maximize the benefits of code scan tools and improve your organization’s security posture.
5.1. Integrating with the Software Development Lifecycle (SDLC)
Why is it crucial to integrate code scan tools into the SDLC? Integrating code scan tools into the Software Development Lifecycle (SDLC) is crucial for ensuring that security is addressed throughout the development process, rather than as an afterthought. This integration allows for early detection and remediation of vulnerabilities, reducing the risk of deploying vulnerable code to production. According to a study by the National Institute of Standards and Technology (NIST), addressing security vulnerabilities early in the SDLC can reduce remediation costs by up to 80%. By integrating code scan tools into the SDLC, organizations can improve their security posture and reduce the overall cost of development.
5.2. Training and Educating Development Teams
How does training development teams enhance the effectiveness of code scan tools? Training and educating development teams on the use of code scan tools is essential for ensuring that they can effectively interpret the results and take appropriate action. This includes providing training on how to use the tool, understand the types of vulnerabilities it detects, and implement remediation strategies. According to a report by the SANS Institute, organizations that invest in security training for their development teams experience a 70% reduction in security incidents. By training development teams on the use of code scan tools, organizations can improve their security posture and reduce the risk of successful attacks.
5.3. Establishing Clear Remediation Processes
Why is it important to establish clear remediation processes for vulnerabilities identified by code scan tools? Establishing clear remediation processes ensures that vulnerabilities identified by code scan tools are promptly and effectively addressed. This includes defining roles and responsibilities for vulnerability remediation, establishing timelines for addressing different types of vulnerabilities, and implementing mechanisms for tracking and verifying remediation efforts. According to a study by Ponemon Institute, organizations with well-defined remediation processes experience a 35% reduction in remediation time. By establishing clear remediation processes, organizations can improve their security posture and reduce the risk of successful attacks.
5.4. Regularly Updating Rules and Signatures
How does regular updating of rules and signatures contribute to the effectiveness of code scan tools? Regularly updating rules and signatures is essential for ensuring that code scan tools remain effective against emerging threats and vulnerabilities. This includes updating the tool’s vulnerability database, adding new rules to detect emerging attack patterns, and fine-tuning existing rules to reduce false positives. According to a report by Gartner, organizations that regularly update their security tools experience a 20% reduction in security incidents. By regularly updating rules and signatures, organizations can improve their security posture and stay ahead of emerging threats.
5.5. Monitoring and Measuring the Effectiveness of Code Scan Tools
Why is it important to monitor and measure the effectiveness of code scan tools? Monitoring and measuring the effectiveness of code scan tools is crucial for ensuring that they are providing the intended security benefits. This includes tracking metrics such as the number of vulnerabilities detected, the time taken to remediate vulnerabilities, and the reduction in security incidents. According to a study by Forrester, organizations that actively monitor and measure the effectiveness of their security tools experience a 15% reduction in operational costs. By monitoring and measuring the effectiveness of code scan tools, organizations can identify areas for improvement and ensure that they are getting the most value from their investment.
6. The Future of Code Scanning
What trends are shaping the future of code scanning technology? The future of code scanning is being shaped by trends such as the increasing use of artificial intelligence (AI) and machine learning (ML) to improve vulnerability detection, the integration of code scanning with cloud-native development environments, and the growing emphasis on DevSecOps practices. AI and ML algorithms are being used to analyze code for complex patterns and anomalies, improving the accuracy and efficiency of vulnerability detection. The integration of code scanning with cloud-native development environments allows for seamless security testing in dynamic and scalable environments. The growing emphasis on DevSecOps practices promotes collaboration between development, security, and operations teams, enabling faster and more effective vulnerability remediation.
6.1. AI-Powered Vulnerability Detection
How is AI transforming vulnerability detection in code scanning? AI is transforming vulnerability detection by enabling code scan tools to analyze code for complex patterns and anomalies that may indicate security flaws. Machine learning algorithms can be trained to recognize common vulnerability patterns and predict potential vulnerabilities based on code characteristics. According to a report by Gartner, AI-powered security tools can improve vulnerability detection accuracy by up to 25%. By leveraging AI, code scan tools can more effectively identify and address security risks, improving the overall security posture of organizations.
6.2. Cloud-Native Security Scanning
What are the benefits of integrating code scanning with cloud-native development environments? Integrating code scanning with cloud-native development environments allows for seamless security testing in dynamic and scalable environments. Cloud-native security scanning tools can automatically adapt to changes in the environment and provide continuous monitoring of code for vulnerabilities. According to a study by the Cloud Security Alliance, organizations using cloud-native security tools experience a 20% reduction in security incidents. By integrating code scanning with cloud-native development environments, organizations can improve their security posture and ensure that their cloud-based applications are protected against emerging threats.
6.3. The Rise of DevSecOps Practices
How does the adoption of DevSecOps practices impact code scanning? The adoption of DevSecOps practices promotes collaboration between development, security, and operations teams, enabling faster and more effective vulnerability remediation. DevSecOps integrates security into every stage of the software development lifecycle, ensuring that security concerns are addressed proactively. According to a report by the DevOps Research and Assessment (DORA) group, organizations that adopt DevSecOps practices experience a 50% reduction in security incidents. By embracing DevSecOps, organizations can improve their security posture and ensure that their software development processes are secure by design.
7. CAR-TOOL.EDU.VN: Your Partner in Code Security
Looking for reliable information on code scan tools and automotive repair solutions? CAR-TOOL.EDU.VN provides detailed comparisons, reviews, and expert advice to help you choose the best tools for your needs. Our comprehensive resources cover a wide range of topics, including vulnerability detection, security scanning, and proactive threat mitigation.
7.1. Expert Advice and Comparisons
Why should you rely on CAR-TOOL.EDU.VN for expert advice on code scan tools? CAR-TOOL.EDU.VN offers expert advice and comparisons to help you make informed decisions about code scan tools. Our team of experts provides detailed reviews and analyses of various tools, highlighting their strengths and weaknesses. We also offer comparisons of different tools, allowing you to easily evaluate your options and choose the best tool for your specific needs. By relying on CAR-TOOL.EDU.VN, you can ensure that you are making informed decisions about code security.
7.2. Comprehensive Resources for Automotive Repair
What other resources does CAR-TOOL.EDU.VN offer for automotive repair professionals? In addition to code scan tools, CAR-TOOL.EDU.VN provides comprehensive resources for automotive repair professionals. Our website offers detailed information on a wide range of automotive tools and equipment, as well as expert advice on repair techniques and best practices. We also offer comparisons of different tools, allowing you to easily evaluate your options and choose the best tools for your specific needs. By visiting CAR-TOOL.EDU.VN, you can access a wealth of resources to help you succeed in the automotive repair industry.
8. FAQs About Code Scan Tools
Do you have questions about code scan tools? Here are some frequently asked questions to help you better understand these essential security tools.
8.1. What types of vulnerabilities do code scan tools detect?
Code scan tools detect a wide range of vulnerabilities, including hard-coded passwords, API keys, SQL injection flaws, cross-site scripting (XSS) vulnerabilities, and other security issues. These tools use various techniques, such as static analysis, dynamic analysis, and heuristic analysis, to identify potential security flaws in code. By detecting these vulnerabilities, code scan tools help organizations improve their security posture and reduce the risk of successful attacks.
8.2. How often should I run code scans?
You should run code scans as frequently as possible, ideally as part of your CI/CD pipeline. This ensures that every code change is checked for vulnerabilities before it is deployed to production. Running code scans on a regular basis allows you to identify and address security issues early, reducing the risk of deploying vulnerable code.
8.3. Can code scan tools eliminate all vulnerabilities?
While code scan tools can detect a wide range of vulnerabilities, they cannot eliminate all security risks. Some vulnerabilities may be too complex for automated tools to detect, and new vulnerabilities are constantly emerging. Therefore, it is important to use code scan tools as part of a layered security approach, along with other security measures such as manual code reviews and penetration testing.
8.4. Are open source code scan tools as effective as commercial tools?
Open source code scan tools can be as effective as commercial tools, but they may require more technical expertise to implement and maintain. Open source tools offer flexibility and customization, allowing organizations to tailor the tool to their specific needs. However, they may not offer the same level of support and ease of use as commercial tools.
8.5. How do I choose the right code scan tool for my organization?
To choose the right code scan tool, start by assessing your development environment and defining your security requirements. Evaluate different tools based on factors such as language support, integration capabilities, scalability, and ease of use. Consider both open source and commercial options, and choose the tool that best fits your budget, technical capabilities, and security needs.
8.6. What is the difference between SAST and DAST?
SAST (Static Application Security Testing) analyzes source code for vulnerabilities without executing the code, while DAST (Dynamic Application Security Testing) analyzes running applications for vulnerabilities by simulating attacks. SAST is typically used early in the development process to identify vulnerabilities in code, while DAST is used later in the process to identify vulnerabilities in running applications.
8.7. How do I integrate a code scan tool into my CI/CD pipeline?
To integrate a code scan tool into your CI/CD pipeline, you can use a plugin or extension provided by the tool vendor, or you can use a command-line interface to execute the tool as part of your build process. Configure the tool to automatically scan code when a new build is triggered, and configure the build to fail if any high-severity vulnerabilities are detected.
8.8. What are some best practices for remediating vulnerabilities identified by code scan tools?
Best practices for remediating vulnerabilities include prioritizing vulnerabilities based on severity and impact, assigning remediation tasks to the appropriate developers, implementing code fixes and security patches, and verifying that the vulnerabilities have been successfully remediated. It is also important to establish clear remediation processes and timelines to ensure that vulnerabilities are addressed promptly and effectively.
8.9. How do I reduce false positives in code scan results?
To reduce false positives, you can customize the rules and policies of the code scan tool to align with your organization’s security requirements and compliance standards. You can also fine-tune the tool’s configuration to reduce the sensitivity of certain rules, and you can use techniques such as static analysis and dynamic analysis to verify the accuracy of the results.
8.10. What is the role of DevSecOps in code scanning?
DevSecOps integrates security into every stage of the software development lifecycle, including code scanning. DevSecOps practices promote collaboration between development, security, and operations teams, enabling faster and more effective vulnerability remediation. By embracing DevSecOps, organizations can improve their security posture and ensure that their software development processes are secure by design.
9. Contact Us Today
Need personalized assistance in selecting the right code scan tools for your organization? Contact CAR-TOOL.EDU.VN today for expert advice and comprehensive solutions. Our team of professionals is ready to help you enhance your code security and protect your valuable assets.
Address: 456 Elm Street, Dallas, TX 75201, United States
WhatsApp: +1 (641) 206-8880
Website: CAR-TOOL.EDU.VN
Don’t wait—secure your code with CAR-TOOL.EDU.VN today!
